

SaaS Security Posture Management (SSPM): The Definitive 2026 Guide
.png)
SaaS Security Posture Management (SSPM): The Definitive 2026 Guide
Discover the core concepts of SaaS security posture management (SSPM). Learn expert strategies to protect your digital assets effectively.
.png)

“Nearly 40% of companies use more than 100 SaaS applications, but less than half track them effectively,” notes a recent Gartner study. As businesses expand their tech stacks, each new tool adds another security checkpoint and another potential risk.
That’s why SaaS security posture management (SSPM) has become a must-have. It’s not just about preventing breaches; it’s about creating a system that keeps your applications compliant, monitored, and protected from day one. Whether you’re a CISO, IT admin, or compliance lead, understanding how to strengthen your SaaS security posture can make a measurable difference in your organization’s risk control and efficiency.
What is SaaS security posture management?
SaaS Security Posture Management is a solution that monitors and manages the security of SaaS applications. It detects misconfigurations, removes unused accounts, and ensures compliance. Continuously scanning for vulnerabilities, SSPM helps prevent breaches and reduces the operational effort needed to maintain SaaS security.
The importance of SaaS security posture management
As companies increasingly rely on a myriad of SaaS products, the complexity of managing security settings across these platforms grows exponentially. An effective security management system provides a centralized platform for IT and security teams to enforce consistent security policies, rectify risky configurations in real time, and automate remediation processes.
The right SaaS security posture management also ensures that your use of SaaS applications aligns with the best security practices and complies with relevant regulations. It's not just about protection; it’s about smart, proactive management of your digital tools to prevent security issues before they become real problems.
SSPM vs. CASB vs. CSPM: What’s the Difference?
Managing SaaS and cloud environments means using the right security tools for each layer. While SaaS Security Posture Management (SSPM), Cloud Access Security Broker (CASB), and Cloud Security Posture Management (CSPM) sound similar, they protect different parts of your cloud ecosystem.
Together, they form a complete SaaS security stack that helps businesses monitor, control, and secure their digital assets across all platforms.
SSPM (SaaS Security Posture Management)?
SSPM focuses on securing SaaS applications. It monitors app settings, permissions, and access controls to detect misconfigurations or compliance issues. It also helps reduce risk by removing unused accounts and fixing security gaps before they become threats.
CASB (Cloud Access Security Broker)?
CASB acts as a gatekeeper between users and cloud applications. It enforces security policies, monitors data transfers, and identifies risky activity. CASBs are crucial for managing user behavior and ensuring safe access to approved tools in the cloud.
CSPM (Cloud Security Posture Management)?
CSPM protects cloud infrastructure such as AWS, Azure, or GCP. It scans for misconfigurations, ensures compliance with security frameworks, and automates remediation across Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) environments.
SSPM vs. CASB vs. CSPM: Comparison
The Five Pillars of Effective SaaS Security Posture Management
A strong SaaS security strategy starts with visibility and control across every application your team uses. The five pillars of SaaS Security Posture Management (SSPM) form the foundation for preventing SaaS misconfigurations, managing identities, and ensuring compliance at scale.
Let’s break down the core SSPM features that keep your cloud environment secure and compliant.
1. Configuration Management
Every SaaS app comes with hundreds of security settings from file-sharing permissions to MFA enforcement. SSPM continuously reviews these configurations to identify weak points and flag risky setups. By automating checks and alerts, you can fix SaaS misconfigurations before they lead to exposure or data loss.
2. Identity and Access Governance
Access control is one of the biggest challenges in SaaS security. SSPM ensures that users only have the permissions they need. It monitors identity settings, tracks role-based access, and highlights overprivileged accounts. This helps reduce the risk of insider threats and unauthorized data sharing.
3. Threat Detection & Monitoring
Modern SSPM tools go beyond configuration checks. They continuously monitor activity across connected apps, detect anomalies, and alert your team to suspicious behavior. This proactive visibility helps security teams catch threats early before they turn into breaches.
4. Third-Party App Management
Third-party integrations can extend functionality but also increase risk. SSPM identifies all connected applications, evaluates their permissions, and flags those that might expose sensitive data. This third-party app risk management feature gives you full visibility into what’s connected to your SaaS ecosystem and where potential risks lie.
5. Governance, Risk, and Compliance
Compliance frameworks like SOC 2, ISO 27001, and GDPR demand strict control over your SaaS stack. SSPM simplifies this by mapping app configurations to compliance standards, tracking audit logs, and generating automated reports. It ensures your organization stays compliant without the manual overhead.
Top 5 Benefits of Using SaaS Security Posture Management
As organizations rely on dozens or even hundreds of SaaS tools, maintaining security across every platform becomes a major challenge. In fact, Gartner predicts that by 2026, 80% of data breaches will be caused by misconfigured SaaS applications.
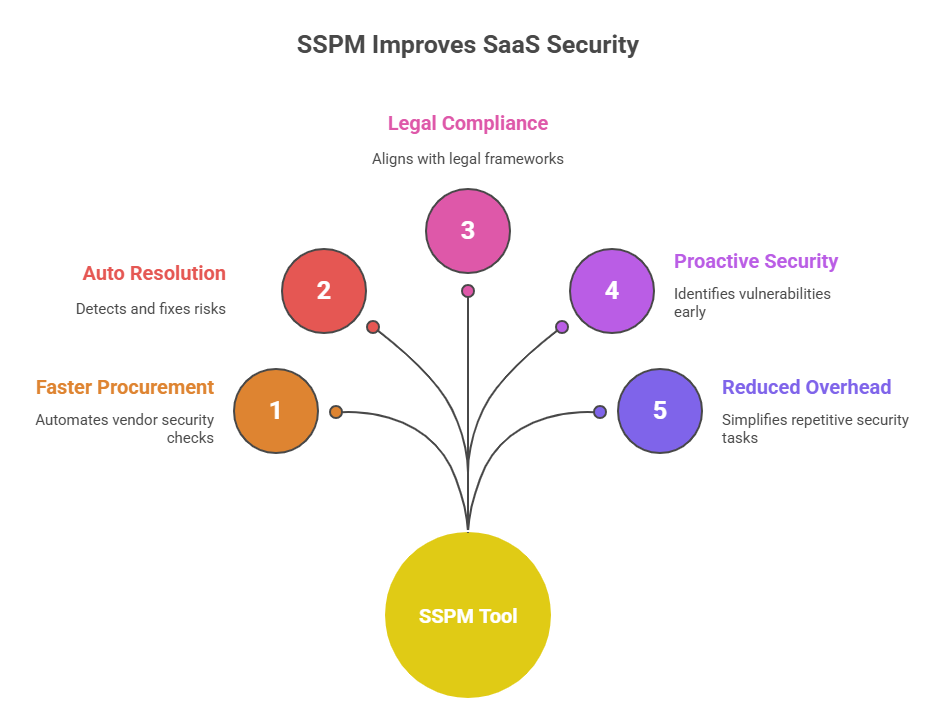
That’s where SaaS Security Posture Management (SSPM) comes in. These platforms help businesses detect risks, ensure compliance, and manage security more efficiently. Here are five key benefits of using SSPM in your organization.
1. Accelerate Your Procurement Cycle
SaaS procurement often slows down because of lengthy vendor security checks. SSPM tools automate the evaluation process by instantly scanning vendors for compliance and risk posture.
This means faster approvals, quicker integrations, and up to 40% shorter procurement cycles according to industry benchmarks.
2. Resolve Security Concerns Automatically
Modern SSPM systems detect and fix risks in real time. They continuously monitor vendor compliance, flag issues, and even auto-remediate simple misconfigurations.
This proactive automation can cut incident response times by 60%, improving coordination between IT, security, and procurement teams.
3. Ensure Complete Legal Compliance
Compliance failures are costly, non-compliance penalties can reach $14 million per incident on average (IBM, 2024). SSPM tools automatically align your app settings with frameworks like SOC 2, ISO 27001, and GDPR.
They also generate audit-ready reports, helping you stay compliant without adding extra workload or risk.
4. Stay Proactive About Your SaaS Security Posture
Instead of reacting to security incidents, SSPM helps teams anticipate them. With real-time dashboards and anomaly detection, security leaders can identify vulnerabilities before they’re exploited.
Organizations that use SSPM report 30% fewer misconfigurations and better cross-team visibility into SaaS usage and risk.
5. Reduce Operational Overhead and Focus on Strategy
SSPM simplifies repetitive security tasks like configuration checks and report generation. By automating these, IT and security teams free up time for strategic work such as vendor negotiations or tool optimization.
On average, companies see a 25–35% reduction in manual security workload after deploying SSPM.
How SaaS Security Posture Management (SSPM) Works
SaaS Security Posture Management (SSPM) keeps your cloud applications secure by continuously monitoring them for risks such as misconfigurations, excessive permissions, and compliance gaps.
Using API-based connections, SSPM scans your SaaS tools like Salesforce, Google Workspace, and Microsoft 365 to detect issues that could expose sensitive data. When a deviation from your security baseline occurs, the system alerts administrators and provides either step-by-step guidance or automated fixes. The result: a stronger, more resilient SaaS environment.
Core Functions of SSPM
1. Continuous Monitoring: SSPM provides real-time visibility into every connected application. It continuously scans for security risks across identities, permissions, configurations, and integrations helping teams catch issues before they escalate.
2. Risk Assessment: It evaluates each configuration and user setting against established security benchmarks and standards, such as CIS or ISO. Risks are then prioritized by severity and potential business impact, helping teams focus on what matters most.
3. Misconfiguration Detection: Misconfigurations are one of the top causes of SaaS breaches. SSPM automatically identifies risky settings like public file sharing or unrestricted access controls, ensuring your data stays private and secure.
4. User Permission Analysis: By analyzing user roles and access levels, SSPM ensures everyone has only the permissions they need. It flags unnecessary privileges and highlights inactive accounts that should be removed supporting the principle of least privilege.
5. Compliance Checks: SSPM constantly reviews your SaaS environment against compliance requirements such as GDPR, HIPAA, and SOC 2. It identifies settings that could trigger violations, helping your organization stay compliant without manual effort.
6. Integration Security: Every third-party integration adds another potential risk. SSPM audits these connections to verify they meet security standards and flags those with unsafe permissions or weak authentication.
7. Drift Detection: Configurations can change over time. SSPM detects when settings drift from your approved security baseline and immediately alerts the team, ensuring continuous alignment with security policies.
8. Remediation: Once an issue is identified, SSPM helps fix it quickly. Admins receive clear guidance for resolution, or the system can automatically take corrective action like revoking access, updating permissions, or disabling inactive accounts.
How SSPM Streamlines Secure SaaS Onboarding
Onboarding new SaaS vendors can be risky if not managed carefully. Each new tool introduces potential vulnerabilities from unverified integrations to unclear access policies. A SaaS Security Posture Management (SSPM) platform ensures every step of your SaaS vendor onboarding process is secure, compliant, and transparent.
Here’s how an SSPM simplifies and safeguards SaaS onboarding from start to finish.
1. Automated Vendor Risk Assessment
Before approving a new SaaS vendor, an SSPM tool performs a comprehensive security risk assessment through API-level scans. It evaluates the vendor’s configuration, compliance posture, and data handling practices.
This SSPM vendor risk assessment helps your security team spot red flags like weak encryption, over-permissive access, or integration vulnerabilities before the tool is approved for use.
2. Policy Enforcement During Onboarding
Once a vendor passes the initial review, SSPM enforces your security and access policies automatically. It applies standardized rules for authentication, data storage, and permission controls across all SaaS tools.
This ensures that every new vendor aligns with your organization’s security framework from day one, reducing manual oversight and human error.
3. Continuous Monitoring After Integration
Security doesn’t end once a vendor is approved. SSPM provides continuous monitoring after onboarding to detect configuration drift, compliance gaps, or changes in data access.
With real-time alerts and automated remediation workflows, teams can address potential issues before they become threats keeping SaaS vendor onboarding security consistent and reliable over time.
4. Secure Integration With Existing Systems
SSPM also reviews API connections and data flow between your SaaS vendors and internal systems. It identifies insecure endpoints, verifies encryption protocols, and ensures integrations don’t expose sensitive information.
This visibility helps IT and security teams maintain control without slowing down deployment.
5. Ongoing Compliance and Reporting
Post-onboarding, SSPM tools automatically map vendor configurations to compliance frameworks like SOC 2, ISO 27001, and GDPR. Built-in dashboards generate detailed reports that make audits faster and easier, saving time while maintaining accountability.
Centralized security management with Spendflo
The more SaaS tools your business adopts, the harder it becomes to stay secure. Each new app brings another vendor, another data flow, and another risk. Without centralized control, even small misconfigurations can lead to big compliance issues or costly breaches.
That’s why growing companies are turning to Spendflo.
One finance-led enterprise recently used Spendflo’s Vendor Management and Third-Party Risk Assessment features to consolidate over 90 SaaS vendors into a single dashboard. Within three months, they cut onboarding time by 35%, eliminated redundant apps, and closed compliance gaps that had been missed for two audit cycles.
This kind of visibility matters because SaaS risk doesn’t stop at onboarding. As your stack grows, vendors change permissions, integrations drift, and compliance standards evolve. Without continuous monitoring, those changes can quietly expose your organization to risk.
Spendflo solves this by giving you a single, secure platform to manage every vendor relationship from procurement to compliance. Automated risk assessments, policy enforcement, and real-time alerts help your team move faster and stay protected.
If you’re ready to simplify SaaS security and bring all your vendor data under one roof, Spendflo can help.
Book a demo today to see how you can gain full visibility, reduce risk, and secure your SaaS ecosystem with confidence.
Frequently Asked Questions
1. How does SSPM differ from CASB and CSPM?
While all three tools strengthen cloud security, they focus on different layers. SaaS Security Posture Management (SSPM) protects SaaS applications by monitoring configurations, permissions, and compliance. Cloud Access Security Broker (CASB) secures data in motion between users and cloud services, enforcing access policies. Cloud Security Posture Management (CSPM) safeguards the underlying infrastructure like AWS, Azure, or Google Cloud by detecting and correcting misconfigurations. Together, they create a complete cloud security stack covering applications, data, and infrastructure.
2. Why is SSPM important for businesses?
As companies adopt more SaaS tools, visibility and control often become fragmented. SSPM helps close these gaps by continuously monitoring for risks such as misconfigurations, excessive permissions, and compliance violations. It ensures that every app in your stack meets security and regulatory standards, reducing exposure to data breaches and financial penalties. Beyond security, SSPM also improves efficiency by automating checks and providing clear, actionable reports for IT and compliance teams.
3. How can I get started with SSPM?
The best way to begin is by mapping your current SaaS environment, understanding which applications are in use, how data flows between them, and where access controls may be weak. From there, implementing an SSPM solution like Spendflo gives you centralized visibility and automated protection. Spendflo helps you assess vendor risk, enforce security policies, and monitor configurations continuously.















.png)
.png)















